Firmware Updates with Dell OpenManage Essentials (OME)
The device discovery part turns out to be much easier than expected, probably due to the firmware on all my hardware has been updated recently and snmp has been setup correctly as well.
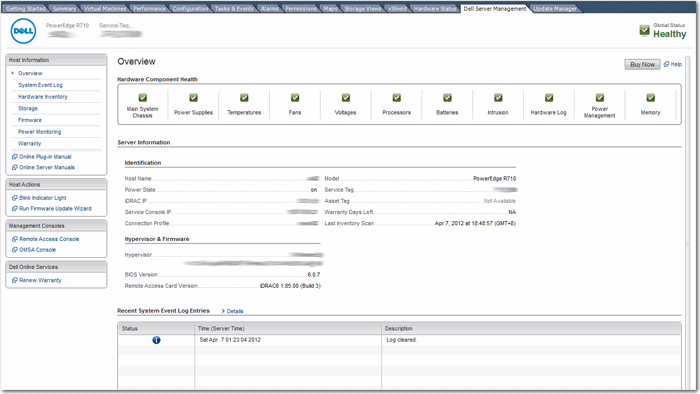
After you set the IP range and snmp community strings under Discovery and Inventory, OME quickly collects all the Poweredge Servers, Equallogic Arrays, PowerConnect Switches, PowerVault Arrays as well as finding the corresponding iDrac and OpenManage address automatically.
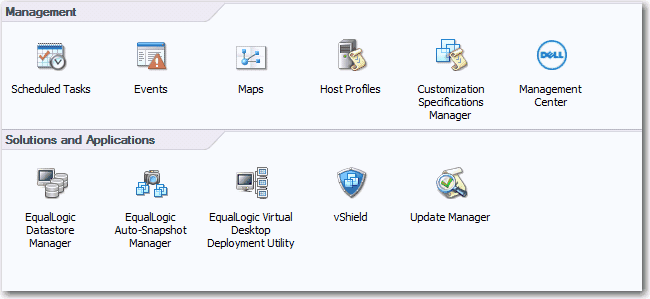
In fact Dell OpenManage Essentials (OME) is simply a central portal that collects every device in your network, you can view and manage them from one window and best you can receive server fault alert via email, it serves the same purpose as the previous long live Dell IT Assistant but MUCH BETTER!
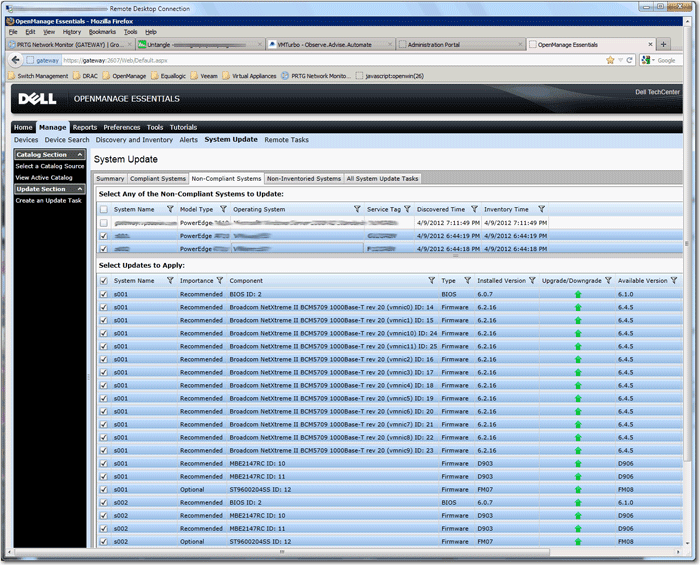
One of the Best Feature IMOO is System Update (BIOS/Firmware) under Manage for your ESX servers, it automatically pulls the latest firmware catalog from Dell’s FTP and compares with your server firmware level and list out all the latest one for you to choose from, it even pull the hard disk firmware to be precise!
I haven’t test and perform the update yet, but I guess it’s the same theory that System Update will ultilize iDrac and USC to patch your system’s BIOS and various firmware, but I guess it won’t automatically put your ESX to maintenance mode first, for that I think you need to manually do it yourself.
So there is no need to use Repository Manager any more, saving lots of time to build your own catalog and no need to use Dell Management Plugin for VMware vCenter (DMPVV) – that’s why I’ve been emphasizing Dell should make it free of charge.
Some other interesting features including OME can automatically pull the Warranty Information based on Service Tag it gathered from Dell and report very detail hardware information regarding the servers in its inventory.
Finally some words about License Manager that includes with OME, I found it will collect all your iDrac 7 license information and manage from one console. Howerver, it works for 12the generation Poweredge Server and iDrac 7 only which I don’t have any currently, so I’ve uninstalled it.
Btw, since when does Dell start to copy HP and charge remote console KVM license just like iLo? ![]()
Anyway, I do think Dell OpenManage Essentials (OME) will replace ITA shortly (in my case, I think I will get rid of ITA tomorrow) and it’s a solid management tool for every Dell server administrator.
Update April 14, 2012
I’ve completely re-configured everything on OEM, it’s much easier and most importantly, it discover the inventory and SNMP traps much faster than IT Assistant, so my ITA can finally retire. Thank you very much Dell for making a great product for free!
Update April 18, 2012
How to Configure SNMP Trap Destinations on Linux Server
For OpenManage Essentials to display alerts for a device, you must configure the device to send traps to the OpenManage Essentials server.
To configure a trap destination:
1. Open the file for editing:
/etc/snmp/snmpd.conf
2. Add the following line to the file:
Trapsink <OME IP Address> <community name>
where IP_address is the IP address of the management station and community_name is the SNMP community name
3. To enable the changes, restart the SNMP agent:
/etc/init.d/snmpd restart
Note – this step is only needed once after all configuration changes are completed.
Update June 23, 2021
After almost 10 years, the latest OME Catalog.cab update cannot be applied due to format has been changed for OME version 1.01 as it always falsely shows the latest signature is 03/06/2012.
Originally I thought the only way to update it is manually download the latest update signature from https://downloads.dell.com/catalog/catalog.cab, then use Select a Catalog Source > Use repository manager file, browse to the saved catalog.cab.
But it turned out the catalog format has been changed since, so only solution is to get the latest version 2.5 (1GB size).
In fact OME (OpenManage Essentials) 2.5 is going to be the last version, and moving to OpenManage Enterprise for DellEMC devices.